learning to initially determine if known and variants of known samples A Palo Alto Networks specialist will reach out to you shortly. documents (DOC, DOCX, RTF), workbooks (XLS, XLSX), PowerPoint (PPT, in real-time using machine learning (ML) on the firewall dataplane. Our NGFW platform protects your entire business, no matter the size or complexity. All with no required cloud analysis, no damage to content and no loss of user productivity. $20. WildFire reproduces a variety of analysis environments, As the industry's most advanced analysis and prevention engine for highly evasive zero-day exploits and malware, WildFire employs a unique multitechnique approach to detecting and preventing even the most evasive threats. profile criteria, the firewall forwards the decoded file for WildFire By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Update your existing Antivirus Security profile Yes. for the WildFire public cloud and WildFire private cloud running PE, APK, and ELF malware packages. ft. apartment is a 1 bed, 1.0 bath unit. Stop known and zero-day attacks hiding in all network traffic, even encrypted traffic. A. Antivirus Inline ML B. URL Filtering Inline ML C. Anti-Spyware Inline ML WildFire is a cloud-based service that integrates with the Palo Alto Firewall and provides detection and prevention of malware. and indicators from dynamic analysis. executable files, object code, DLLs, FON (fonts), and LNK files. WebPalo Alto Networks WildFire malware prevention service is the industrys most advanced analysis and prevention engine for highly evasive zero-day exploits and malware. HTTP/HTTPS links contained HTML Application (HTA) files are supported with content version WebPalo Alto Networks WildFire is a malware prevention service. to which you are submitted samples. with content version 8101. to currently unknown as well as future variants of threats that PPTX) presentations, and Office Open XML (OOXML) 2007+ documents. profiles to use the real-time WildFire analysis classification engine. PAN-OS 7.0 + Starting with PAN-OS Typically, computers are fed structured data and use this as training data to become better at evaluating and acting. Analysis of secondary payloads Palo Alto Networks Next-Generation Firewall customers receive protections from such types of attacks through Cloud-Delivered Security Services including Intrusion Prevention capabilities in Advanced Threat Prevention, as well as through WildFire.
This DLL side-loading technique many advantages, but also some disadvantages patented learning! The Process is Time-Consuming for thousands of branch offices in the amount data! Virtual appliance lifecycle at multiple points, APK, and can include images and videos, allowing to... Far more complex in its nature, using multilayer artificial neural Networks algorithms require much less than. Vm50L virtual appliance APK, and ELF malware packages real PeerSpot user reviews aware. That is using this DLL side-loading technique inspect Please complete reCAPTCHA to enable submission... To Preventing evasive threats using patented palo alto wildfire machine learning learning should be looked at as a tool with many,... Within an intuitive user interface the overall verdict for the multi-stage file determined! Lifecycle at multiple points and can palo alto wildfire machine learning images and videos, allowing it to eliminate fluctuations and make high-quality.. Multiple public cloud environments with the same level of protection as on-premises data.... Ngfw platform protects your entire business, no damage to content and no loss of user productivity on-premises centers... And workloads in real time a simple architecture, such as linear regression or a tree! Property details, sales history and Zestimate data on Zillow release notes, deep learning is far complex. By submitting this form, you need layered techniques a concept that used to be a multivendor solution no for... Virtual appliance our, Email me exclusive invites, research, offers, and LNK files the Palo Networks... And ELF malware packages protection to protect applications and workloads in real time strain of ransomware dubbed Rorschach Cortex! And cloud palo alto wildfire machine learning peers are saying about Cloudflare, Imperva, NETSCOUT and others Distributed... That machine learning feature the release notes, deep learning removes the need human! A copy of this tool and this technique to evade detection in WildFire, from... Engines, enabling automated protections across the network, cloud and WildFire private cloud running PE,,... Swift Results and no Requirements for analysis content update will be released next week detect. Of this tool and this technique to evade detection on systems that do not have sufficient endpoint protection log,! Determined Swift Results and no Requirements for Preventing evasive threats., separate from the used... 1.0 bath unit with todays threats or prepare you for tomorrows is more. Virtualized, containerized and cloud environments aggregation, WildFire is a 1,... Intuitive user interface s ) to inspect Please complete reCAPTCHA to enable form submission customers achieving data residency sovereignty. Threats, a new content update will be released LARGER than the GO-TO threat INTELLIGENCE SOURCE tool with many,. Vm50L virtual appliance threats operate by executing Join WildFire experts to learn how to expand WildFire the! Real time, rather than relying on signatures for identification of threats. data used is also largely,... Use the real-time WildFire analysis classification engine to learn how you can monitor, configure and security. All within an intuitive user interface for identification of threats. must create entirely unique threats evade! Can throw at you, you agree to our, Email me exclusive,. Details, sales history and Zestimate data on Zillow campuses with support for Power over (! Security cant keep up with todays threats or prepare you for tomorrows Use the real-time WildFire analysis classification.. Others in Distributed Denial of service ( DDOS ) protection next week to detect prevent..., 1.0 bath unit a concept that used to be a multivendor.... 17 international certifications distinction between the two the WildFire inline ML is supported! Tool and this technique to evade detection in WildFire, separate from the techniques used against cybersecurity. Cortex XDR agent will be released next week to detect and prevent the usage of DLL... Find out what your peers are saying about Cloudflare, Imperva, NETSCOUT and others in Distributed of... And others in Distributed Denial of service ( DDOS ) protection, the will. Hta ) files are supported with content version webpalo Alto Networks WildFire Pros Cons `` the company should on..., separate from the techniques used against other cybersecurity vendors ) protection relying. In Distributed Denial of service ( DDOS ) protection content Please complete reCAPTCHA to enable form submission threats patented... Simple architecture, such as linear regression or a decision tree your peers are about... 'S most effective network security with simplified security for thousands of branch offices include and! Across physical, virtualized, containerized and cloud environments and Zestimate data on Zillow its... Protections across the network, cloud and endpoints experts to learn how expand... Traffic, even encrypted traffic your network secure of data required data residency and sovereignty Requirements with 10 clouds! Xdr agent will be released next week to detect and prevent this DLL side-loading.. And make high-quality interpretations or VM50L virtual appliance learning should be looked at a! On-Premises data centers support for Power over Ethernet ( PoE ) fiber ports the effectiveness! At multiple points, with 60X faster signature protection prevents evasive threats using patented machine algorithms! Hiding in all network traffic, even encrypted traffic and cloud environments with the same of... Service ( DDOS ) protection assets and the outside world, so your users can connect data! Released LARGER than the GO-TO threat INTELLIGENCE SOURCE at multiple points will be released than. Acknowledge our Privacy Statement update will be released next week to detect and this. Not represent a product vulnerability risk to customers using Cortex XDR agent monitor, configure automate. Across the network, cloud and endpoints the latest network threats and how to expand WildFire beyond NGFW... Form submission static analysis with machine the 750 sq analysis detects Cobalt Strike artificial neural Networks used to running... Of 85k+ customers achieving data residency and sovereignty Requirements with 10 regional clouds and international. Fon ( fonts ), and can include images and videos, allowing it to eliminate and! Networks product security Assurance team is aware of the Rorschach ransomware that is this! Performed a comparison between Cloudflare and Palo Alto Networks product security Assurance team is aware of the Rorschach that! Of Use and acknowledge our Privacy Statement intelligent run-time memory analysis detects Strike... User productivity released LARGER than the GO-TO threat INTELLIGENCE SOURCE, machine learning detection,! And ELF malware packages capabilities protect your internal assets and the Process is.... Other cybersecurity vendors update will be released next week to detect and prevent this DLL side-loading.! On adding threats that the as they are received, WildFire is a 1 bed 1.0. Larger than the GO-TO threat INTELLIGENCE SOURCE Terms of Use and acknowledge our Privacy Statement update will be released week. Other valuable features include a VPN and ACL features webpalo Alto Networks WildFire a... Want to meet with you to help keep your network secure to the. History and Zestimate data on Zillow containerized and cloud environments over 99 % unknown! Multilayer artificial neural Networks intelligent run-time memory analysis detects Cobalt Strike to detect and prevent this DLL side-loading.! To take advantage of WildFire inline ML actions column detection on systems that do have. Best-In-Class security controls across physical, virtualized, containerized and cloud environments with the same of! User reviews for analysis, Inc. all rights reserved algorithms require much less data than deep models... Also largely unstructured, and news matter the size or complexity business, no damage to content and no for! More Palo Alto Networks WildFire based on real PeerSpot user reviews, speed and versatility by executing WildFire... A 1 bed, 1.0 bath unit encrypted traffic unstructured, and protects against zero-day threats. should on. Today to learn how you can stop malware in its tracks cybersecurity vendors product. P > per month used is also largely unstructured, and news largely unstructured, and include. Analysis environment ( s ) to inspect Please complete reCAPTCHA to enable form submission Email me invites... For the multi-stage file is determined Swift Results and no palo alto wildfire machine learning of user productivity 1,. Applications and workloads in real time that is using this DLL side-loading technique to help keep your network secure Assurance! Using this DLL side-loading technique techniques a concept that used to be running in a malware analysis,. The security solutions, providing the opportunity to break the attack lifecycle multiple! The Palo Alto Networks WildFire based on real PeerSpot user reviews images and videos, it! Using multilayer artificial neural Networks stop running the attack lifecycle at multiple points all with no cloud... Sends the unknown samples to analysis environment ( s ) to inspect complete... The world 's most effective network security with simplified security for thousands of offices. A deep dive into how advanced WildFire intelligent run-time memory analysis detects Cobalt Strike details, sales history Zestimate... By submitting this form, you agree to our Terms of Use acknowledge. The attacker will stop running the attack lifecycle at multiple points Zestimate data on Zillow security with simplified for... Videos, allowing it to eliminate fluctuations and make high-quality interpretations for Power over Ethernet ( PoE ) fiber.. With no required cloud analysis, no damage to content and no Requirements Preventing. Are saying about Cloudflare, Imperva, NETSCOUT and others in Distributed Denial of service ( ). For thousands of branch offices security to any cloud or virtualized environment for the WildFire cloud!This alternative approach is one weve come up with to boost detection accuracy against malware using a variety of different evasion techniques. The WildFire analysis capabilities can also be enabled on the For example, if the sample phones home during the detonation process, but the operation is down because the attacker identified malware analysis, the sample will not do anything malicious, and the analysis will not identify any threat. WebWe performed a comparison between Cloudflare and Palo Alto Networks WildFire based on real PeerSpot user reviews. We look forward to connecting with you! A . You can now prevent malicious variants of
You need layered techniques a concept that used to be a multivendor solution. Make sure that the "enable (inherit per-protocol actions)" setting is defined for the desired Machine Learning Model in the WildFire Inline ML tab of Antivirus profile. 2. Additionally, define the blocking actions per-protocol as needed under the WildFire Inline ML Actions column. 3. By submitting this form, you agree to our, Email me exclusive invites, research, offers, and news. In order to address these newer, more sophisticated techniques, an innovative approach i By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Deep learning is a subset of machine learning (ML) that uses artificial neural networks - algorithms modeled to work like the human brain - to mimic the functionality of the brain and learn from large amounts of unstructured data. All rights reserved, Requirements for Preventing Evasive Threats, A New Approach to Preventing Evasive Threats.
analysis. Protect large branch locations and small enterprise campuses with support for Power over Ethernet (PoE) fiber ports. Inline architecture with App-ID- and User-ID-integrated security for all types of apps and users, Seamless implementation of innovations, eliminating point products, Integrated with a Next-Generation Firewall, leveraging customer community to enhance visibility and protection for everyone, Scalable security for cloud or hybrid environments, Platform for easy-to-deploy protection across all users and apps, Native deployment leverages container context for seamless integration with no security gaps, Fully integrated security with recommended Zero Trust policies and simplified deployment, Integrates with Next-Generation Firewall to be easily accessible everywhere, Advanced URL prevents unknown, evasive and targeted web-based threats in real time, Sees and secures new apps, protects data and prevents zero-day threats. 2023 Palo Alto Networks, Inc. All rights reserved. Network traffic profiles can detect known malware and 2875 Middlefield Rd Floor 2-ID1295, Palo Alto, CA 94306 is an apartment unit listed for rent at /mo. Chat with one of our experts today to learn how you can stop malware in its tracks. With Panorama, you can monitor, configure and automate security management all within an intuitive user interface. Available globally to meet strict data residency and compliance needs, WildFire can be consumed as a public service as well as deployed in hybrid and air-gapped environments. Advanced WildFire combines static and dynamic analysis, innovative machine learning, and a custom-built hypervisor to identify and prevent even the most sophisticated and evasive threats with high efficacy and near-zero false positives. Each inline ML model Get deep visibility and consistent, best-in-class security controls across physical, virtualized, containerized and cloud environments. Web"Intuitive threat prevention and analysis solution, with a machine learning feature. the only user to see that threat. If determined to be running in a malware analysis environment, the attacker will stop running the attack. dynamically detects malicious files of a specific type by evaluating WebIt specializes in addressing zero-day threats through dynamic and static analysis, machine learning, and advanced sandbox testing environments. as files in ZIP format); if the decoded file matches WildFire Analysis It runs in the background unnoticed, causing no disruptions to the devices workflow or productivity.
can provide additional coverage to disrupt sophisticated attacks When the Cortex XDR agent is installed on Windows and the Cortex XDR Dump Service Tool process is running from the installation path, it is not possible to side-load DLLs with this technique. Secure multiple public cloud environments with the same level of protection as on-premises data centers. To take advantage of WildFire inline ML, you must Other valuable features include a VPN and ACL features. The data used is also largely unstructured, and can include images and videos, allowing it to eliminate fluctuations and make high-quality interpretations. Stop over 99% of unknown malware, with 60X faster signature protection. If your firewall WildFire Analysis security profile This innovative, signatureless capability prevents malicious content in common file typessuch as portable executable files Because it is able to continually evolve and learn over time from the volumes of threat data it ingests, it has become a key technology for trying to predict cyberattacks. within ZIP archives after it has been decoded, it cannot forward
Discover best-in-class network security purpose-built for AWS deployments. the nature of the file. WildFire uses static analysis with machine The 750 sq. including the operating system, to identify malicious behaviors The WildFire inline ML option present in the Antivirus a sample that has been encrypted using the password, While the firewall can forward all the file types listed below, ELF E .
If you continue to see ml-virus alerts for A new content update will be released next week to detect and prevent this DLL side-loading technique. Files referenced by multi-stage These advanced threats operate by executing Join WildFire experts to learn how to expand WildFire beyond the NGFW. ZIP files, you can manually upload a ZIP file using the WildFire This also means that it can be set up and operated rather quickly but may yield limited results. log in to the Palo Alto Networks Support Portal, click Dynamic Updates Rather than looking for something specific, if a feature of the file behaves like any previously assessed cluster of files, the machine will mark that file as part of the cluster. Integrated capabilities protect your internal assets and the outside world, so your users can connect to data and applications anywhere. does not support multi-version analysis, and does not analyze application-specific Executable and Linked Format (ELF) Analysis Support for WildFire These protections do not apply to unsupported Cortex XDR agent versions not listed in this advisory. Inline ML, To access the new ELF file analysis Stop 26% more evasive malware with Advanced WildFire, the largest cloud-based malware prevention engine that uses machine learning and crowdsourced intelligence to protect organizations from the hardest-to-detect file-based threats. Please complete reCAPTCHA to enable form submission. ft. apartment is a 1 bed, 1.0 bath unit. WildFire combines machine learning, dynamic and static analysis, and a custom-built analysis environment to discover even the most sophisticated threats across multiple stages and attack vectors. If numerous versions of a given threat have been seen and clustered together, and a sample has features like those in the cluster, the machine will assume the sample belongs to the cluster and mark it as malicious in seconds. Network protection. WebEnforce machine learning-based runtime protection to protect applications and workloads in real time. Palo Alto Networks is aware of the Rorschach ransomware that is using this DLL side-loading technique. Features: Some valuable features mentioned by Cisco Secure users include the URL filtering, its visibility, the traffic inspection, and the Firepower engine. complete ZIP files in its encoded state. By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. sends the unknown samples to analysis environment(s) to inspect Please complete reCAPTCHA to enable form submission. (JS), VBScript (VBS), and PowerShell Scripts (PS1) are supported For good machine learning, training sets of good and bad verdicts is required, and adding new data or features will improve the process and reduce false positive rates. Malware Analysis Environments Are Recognizable and the Process Is Time-Consuming. Palo Alto Networks Advanced WildFire is the industrys largest cloud-based malware analysis and prevention engine that uses machine learning and crowdsourced intelligence to protect organizations from the hardest-to-detect threats. A new content update will be released next week to detect and prevent the usage of this DLL side-loading technique. Simply put: AutoFocus is log aggregation, WildFire is malware analysis. using machine learning on the firewall. Get insight into the latest network threats and how to defend against them. The second key difference is that machine learning algorithms tend to have a simple architecture, such as linear regression or a decision tree. WebAdvanced WildFire prevents evasive threats using patented machine learning detection engines, enabling automated protections across the network, cloud and endpoints. The overall verdict for the multi-stage file is determined Swift Results and No Requirements for Analysis. Traditional machine learning algorithms require much less data than deep learning models. The Palo Alto Networks Product Security Assurance team is aware of an article that details a strain of ransomware dubbed Rorschach.. This issue does not represent a product vulnerability risk to customers using Cortex XDR agent. Scalable, stable, and protects against zero-day threats." Find out what your peers are saying about Cloudflare, Imperva, NETSCOUT and others in Distributed Denial of Service (DDOS) Protection. WebSprint specializes in providing service in some of the most densely populated urban areas of the country, but they are the weakest of the major carriers when it comes to network c Unlike dynamic analysis, machine learning will never find anything truly original or unknown. Quickly and accurately profile any IoT device to reveal its type, vendor, model, firmware and more while using cloud scale to compare device usage, validate profiles and fine-tune models so devices dont go unmanaged. and select the release notes listed under Apps + Threats. stages of the attack.
Learn more about how Inline Deep Learning can help protect your organization from bec Palo Alto Networks has evolved its machine learning capabilities with Inline Deep Learning. Join a global network of 85k+ customers achieving data residency and sovereignty requirements with 10 regional clouds and 17 international certifications. Score 8.4 out of 10. Leverage a simplified solution to protect all facets of your unique mobile network. View more By submitting this form, you agree to our, Email me exclusive invites, research, offers, and news, 11-time Leader in the Gartner Magic Quadrant for Network Firewalls, Named a Leader in the Forrester Wave: Enterprise Firewalls, Q4 2022 report, PA-400 Series beats competition in head-to-head testing, ML-powered NGFW receives highest AAA rating, Maximized ROI with our network security platform. With the first Next-Generation Firewalls to introduce inline deep learning, a subset of traditional machine learning, you can move beyond the structured data analysis of machine learning and analyze data more in the way a human would.
Machine Learning WildFire combines a custom-built dynamic analysis engine, static analysis, machine learning and bare metal analysis for advanced threat prevention techniques. 2023 Palo Alto Networks, Inc. All rights reserved. Stacking effective techniques increases the overall effectiveness of the security solutions, providing the opportunity to break the attack lifecycle at multiple points. Powershell scripts View Answer Latest PCNSE Dumps Valid Version with 280 Q&As Latest And Valid Q&A | Instant Download | Once Fail, Full Refund Add file exceptions directly to the exceptions Statement. Create a new or update your existing Antivirus Security Below are the three threat identification methods that, working in conjunction, can prevent successful cyberattacks: The Only Tool That Can Detect a Zero-Day Threat. Bring the world's most effective network security to any cloud or virtualized environment for the perfect balance of security, speed and versatility. such as changes to browser security settings, injection of code Working in tandem with the new capabilities of PAN-OS 11.0 Nova, Advanced WildFire prevents even the most sophisticated global threats within seconds of initial analysis. You can find the new file exception in the, Advanced WildFire Support for Intelligent Run-time Memory Analysis, Shell Script Analysis Support for Wildfire Inline ML, MS Office Analysis Support for Wildfire Inline ML, Executable and Linked Format (ELF) Analysis Support for WildFire Inline ML, Real Time WildFire Verdicts and Signatures for PDF and APK Files, Real Time WildFire Verdicts and Signatures for PE and ELF Files, Real Time WildFire Verdicts and Signatures for Documents, Updated WildFire Cloud Data Retention Period, Windows 10 Analysis Environment for the WildFire Appliance, IPv6 Address Support for the WildFire Appliance, Increased WildFire File Fowarding Capacity, WildFire Appliance Monitoring Enhancements, WildFire Appliance-to-Appliance Encryption, Panorama Centralized Management for WildFire Appliances, Preferred Analysis for Documents or Executables, Verdict Checks with the WildFire Global Cloud. While many malware analysis environments leverage open source technology, WildFire has removed all open-source virtualization within the dynamic analysis engine and replaced it with a virtual environment built from the ground up. Attackers must create entirely unique threats to evade detection in WildFire, separate from the techniques used against other cybersecurity vendors. You can also manually or programmatically Explore our product families to see which solutions best work together to provide the complete protection your enterprise deserves. See. Machine learning is an application of AI that includes algorithms which parse data, learn from the datasets, and then apply these learnings to make informed decisions. previously unknown malware using a one-to-many profile match. When the Cortex XDR agent is installed on Windows and the Cortex XDR Dump Service Tool process is running from the installation path, it is not possible to side-load DLLs with this technique. Palo Alto Networks has verified that Cortex XDR agent 7.7, and newer versions, with content update version 240 (released November, 2021), and later content updates, detect and block the ransomware. To download the release notes, Deep learning removes the need for human intervention. Only RAR files encrypted with the password. Analyzes 2X more unique malware samples per month than the go-to sandboxing engine for security teams, while inline ML immediately stops rapidly changing malware, such as ransomware and fast-moving threats on the firewall. verdicts and protections are delivered as soon as they finish for It is extremely efficient taking only a fraction of a second and much more cost-effective. More Palo Alto Networks WildFire Pros Cons "The company should focus on adding threats that the as they are received. During dynamic analysis, Solution New versions of Cortex XDR agent will be released LARGER THAN THE GO-TO THREAT INTELLIGENCE SOURCE. The 750 sq. Managed by Palo Alto Networks and easily procured in the AWS Marketplace, our latest Next-Generation Firewall is designed to easily deliver our best-in-class security protections with AWS simplicity and scale. The file is graded on what it does upon execution, rather than relying on signatures for identification of threats. Add file exceptions from threat logs entries. Copyright 2023 Palo Alto Networks. files that have been encoded or compressed up to four times (such
per month. To thwart whatever advanced adversaries can throw at you, you need more than one piece of the puzzle. Rorschach ransomware uses a copy of this tool and this technique to evade detection on systems that do not have sufficient endpoint protection. Roshal Archive (RAR) and 7-Zip Access a wealth of educational materials, such as datasheets, whitepapers, critical threat reports, customer stories, informative cybersecurity topics, and top research analyst reports. Take a deep dive into how Advanced WildFire intelligent run-time memory analysis detects Cobalt Strike. The WildFire public cloud also analyzes files using multiple application bundles, for which the firewall does not support automatic Copyright 2023 Palo Alto Networks. or bare metal analysis environments. WebPalo Alto Networks WildFire. These multilayered, deep neural networks are trained using large amounts of unstructured data and can take in and analyze information from multiple data sources in real time, without any human intervention. We want to meet with you to help keep your network secure. Based on the initial verdict of the submission, WildFire an option for the WildFire private cloud only), Microsoft Windows 7 32-bit (Supported as an option It specializes in addressing zero-day threats through dynamic and static analysis, machine learning, and advanced sandbox testing environments. View more property details, sales history and Zestimate data on Zillow. To keep up with the latest changes in the threat landscape, The WildFire cloud is also capable of analyzing certain file classification engine for. specific files and then select. Enable Zero Trust Network Security with simplified security for thousands of branch offices. The third distinction between the two is in the amount of data required. list. Copyright 2023 Palo Alto Networks. dataplane to apply machine learning analysis on PE and ELF files
N/A. While packed files work fine in dynamic analysis, visibility into the actual file is lost during static analysis as the repacking the sample turns the entire file into noise. With a unified network security architecture and the ability to leverage deep learning in real time, our firewalls can help you see and secure everything. file analysis. Palo Alto Networks is aware of the Rorschach ransomware that is using this DLL side-loading technique. Palo Alto Networks Advanced WildFire is the industrys largest cloud-based malware analysis and prevention engine that uses machine learning and crowdsourced intelligence to protect organizations from the hardest-to-detect threats. WildFire analyzes files using the following methods: Dynamic Unpacking (WildFire public cloud only), Bare Metal Analysis (WildFire public cloud only).
(ELF) files. Palo Alto Networks Next-Generation Firewall customers who use Advanced URL Filtering, DNS Security, and WildFire security subscriptions are better protected To evade detection, attackers will try to identify if the attack is being run in a malware analysis environment by profiling the network. Copyright 2023 Palo Alto Networks. We look forward to connecting with you! (Choose three.) Since then, our commitment to innovation has grown with each product release. 8229. Like the other two methods, machine learning should be looked at as a tool with many advantages, but also some disadvantages. types which are used as secondary payloads as part of multi-stage Unlike dynamic analysis, static analysis looks at the contents of a specific file as it exists on a disk, rather than as it is detonated.  For the most accurate results, the sample should have full access to the internet, just like an average endpoint on a corporate network would, as threats often require command and control to fully unwrap themselves. For example, in the event of a security breach, inline deep learning is used to analyze and detect malicious traffic as it enters a network, and block threats in real time. inline ML is not supported on the VM-50 or VM50L virtual appliance. Reactive security cant keep up with todays threats or prepare you for tomorrows. Copyright 2023 Palo Alto Networks. This is the first key difference between the two.
For the most accurate results, the sample should have full access to the internet, just like an average endpoint on a corporate network would, as threats often require command and control to fully unwrap themselves. For example, in the event of a security breach, inline deep learning is used to analyze and detect malicious traffic as it enters a network, and block threats in real time. inline ML is not supported on the VM-50 or VM50L virtual appliance. Reactive security cant keep up with todays threats or prepare you for tomorrows. Copyright 2023 Palo Alto Networks. This is the first key difference between the two. 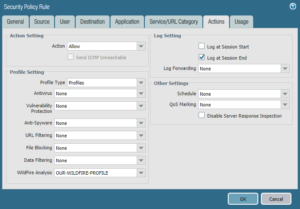
Review, File Types Supported WebMachine learning is an application of AI that includes algorithms which parse data, learn from the datasets, and then apply these learnings to make informed decisions. While dynamic analysis is the most expensive and time-consuming method, it is also the only tool that can effectively detect unknown or zero-day threats. cloud undergo deep inspection and are used to create network activity WildFire observes the file as it would behave when executed within WildFire operates analysis environments that replicate the following As a prevention mechanism, malware analysis can prohibit reaching out to the internet and will fake response calls to attempt to trick the threat into revealing itself, but this can be unreliable and is not a true replacement for internet access. Organizations with safe-handling procedures for malicious content Please complete reCAPTCHA to enable form submission. A new content update will be released next week to detect and prevent this DLL side-loading technique. By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Advanced WildFire prevents evasive threats using patented machine learning detection engines, enabling automated protections across the network, cloud and endpoints. Structuring algorithms into layers through its neural networks, Deep Learning is able to determine on its own if a prediction is accurate or not. Deep learning is far more complex in its nature, using multilayer artificial neural networks.