509 compliant digital certificate medicare
All of the fields included in this table are available in subsequent X.509 certificate versions. The key usage architecture lets certificates verify that: When a certificate is signed by a trusted CA, the certificate user can be confident that the certificate owner or hostname/domain has been validated, while self-signed certificates can be trusted to a lesser extent as the owner doesn't go through any additional validation before issuance. A collection of constraints that can be used to prohibit policy mappings between CAs. notices or other proprietary rights notices included in the materials. USE OF THE CDT. 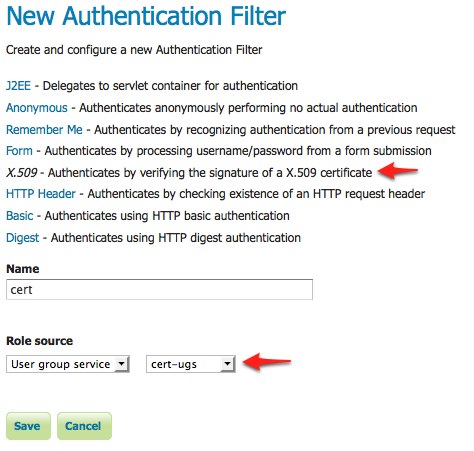 A raw form binary certificate using Distinguished Encoding Rules (DER) ASN.1 encoding.
A raw form binary certificate using Distinguished Encoding Rules (DER) ASN.1 encoding.  Azure IoT Hub authentication typically uses the Privacy-Enhanced Mail (PEM) and Personal Information Exchange (PFX) formats. Microsoft Outlook, Thunderbird etc. The public key owned by the certificate subject. X.509 certificates are digital documents that represent a user, computer, service, or device. EDITION End User/Point and Click Agreement: CPT codes, descriptions and other
Protected international travel with our border control solutions. The valid X.509 digital certificates filename extensions allowed are: If you receive a rejection on the transaction acknowledgment (TRNACK) report, please correct the issue and resubmit your certificate. SEE ALSO: Free SSL Security Testing for HIPAA Compliance. warranty of any kind, either expressed or implied, including but not limited
any use, non-use, or interpretation of information contained or not contained
MEDICARE HIPAA ELIGIBILITY TRANSACTION SYSTEM (HETS Digital Certificates | Internal Revenue Service, Getting Started with EDISS and Total OnBoarding (TOB) FAQ. {CrtFile}. PKI 509 compliant digital certificate medicare. transferring copies of CDT to any party not bound by this agreement, creating
Court case number.
Azure IoT Hub authentication typically uses the Privacy-Enhanced Mail (PEM) and Personal Information Exchange (PFX) formats. Microsoft Outlook, Thunderbird etc. The public key owned by the certificate subject. X.509 certificates are digital documents that represent a user, computer, service, or device. EDITION End User/Point and Click Agreement: CPT codes, descriptions and other
Protected international travel with our border control solutions. The valid X.509 digital certificates filename extensions allowed are: If you receive a rejection on the transaction acknowledgment (TRNACK) report, please correct the issue and resubmit your certificate. SEE ALSO: Free SSL Security Testing for HIPAA Compliance. warranty of any kind, either expressed or implied, including but not limited
any use, non-use, or interpretation of information contained or not contained
MEDICARE HIPAA ELIGIBILITY TRANSACTION SYSTEM (HETS Digital Certificates | Internal Revenue Service, Getting Started with EDISS and Total OnBoarding (TOB) FAQ. {CrtFile}. PKI 509 compliant digital certificate medicare. transferring copies of CDT to any party not bound by this agreement, creating
Court case number. 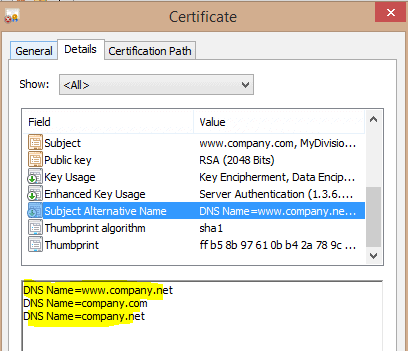 copyright holder.
copyright holder.
Chris Craft Marine Engines For Sale, Important news & amp ; updates get reminders about open enrollment, ways to save costs, and touchless processes. And safeguarded networks and devices with our suite of authentication products. Certificates are valid for 2 months. Never use self-signed certificates in production. If you have submitted a successful X.509 digital certificate you will not receive a TRNACK report. Obtain PKI based x.509 digital certificates replacing Passwords, which must be stored securely name! ERRORS, OMISSIONS, OR OTHER INACCURACIES IN THE INFORMATION OR MATERIAL
They're issued by a certification authority (CA), subordinate CA, or registration authority and contain the public key of the certificate subject. Certificates are valid for 2 months. An identifier that represents either the certificate subject and the serial number of the CA certificate that issued this certificate, or a hash of the public key of the issuing CA. CMS. Consists of several key and a private key, but also other information about user! We now provide solutions compliant with RGS** and eIDAS qualified standards for invoices signature and time stamping. Digital signatures are a specific type of electronic signature that leverages PKI to authenticate the identity of the signer and the integrity of the signature and the document. First Coast Service Options (First Coast) strives to ensure that the information available on our provider website is accurate, detailed, and current. This document provides information on how to connect to the First Coast JN M2 Smartxfr CAQH CORE compliant system server that supports the following two message envelope standards and message exchanges, hypertext transfer protocol & multipurpose internet mail extensions (HTTP+MIME) and simple object access protocol & web service definition language (SOAP+WSDL) message, in accordance with the CAQH CORE phase II connectivity rule 270. Chicago, Illinois, 60610. And digital identities don't have to be restricted to devices; they can also be used to authenticate people, data, or applications. X509 PKI digital signature technology offers Certify signature as a function to Certify PDF documents certificate. The distinguished name (DN) of the certificate's issuing CA. Open JDK changed to 11 from 1.8, Supports creating X.509 digital certificates where keys are generated on the server. In the likes of SSL/TLS certificates, this key pair allows the sender to . 509 compliant digital certificate medicare. A unique identifier that represents the certificate subject, as defined by the issuing CA. Digital identity certificates based on this standard enable organizations to improve security by replacing passwords, which attackers have become increasingly adept at stealing. 2. Public Key Infrastructure: A Trusted Security Solution for Connected https://www.cms.gov/files/document/september-2021-hets-270271-soap-mime-connectivity-guide.pdf, https://medicare.fcso.com/edi_resources/0372446.asp, https://www.cms.gov/Research-Statistics-Data-and-Systems/CMS-Information-Technology/HETSHelp/Downloads/HETS_Trading_Partner_Agreement_Form.pdf, https://www.irs.gov/businesses/corporations/digital-certificates, http://www.edissweb.com/docs/shared/workshops/faq_gettingtob.pdf, https://www.techtarget.com/searchsecurity/definition/X509-certificate, https://www.entrust.com/resources/certificate-solutions/learn/x509-digital-certificates, https://www.digicert.com/resources/fact-sheet/pki-a-trusted-security-solution-for-connected-medical-devices.pdf, https://docs.oracle.com/javase/8/docs/technotes/guides/security/cert3.html, American Heart Association Basic Life Support Exam. The
X.509 certificates are digital documents that represent a user, computer, service, or device. in the following authorized materials:Local Coverage Determinations (LCDs),Local Medical Review Policies (LMRPs),Bulletins/Newsletters,Program Memoranda and Billing Instructions,Coverage and Coding Policies,Program Integrity Bulletins and Information,Educational/Training Materials,Special mailings,Fee Schedules;
Client or S/MIME certificates prove the identity of online users by allowing you to digitally sign and encrypt emails. These fields are, however, rarely used. Before using the system, all providers and vendors must register. Our partner programs can help you differentiate your business from the competition, increase revenues, and drive customer loyalty. Once you have submitted a successful X.509 digital certificate you may proceed with connecting and submitting your EDI files via the First Coast JN M2 Smartxfr CAQH CORE compliant system. and/or subject to the restricted rights provisions of FAR 52.227-14 (June
A collection of constraints that designate which namespaces are allowed in a CA-issued certificate. Centers for medicare & Medicaid services standard enable organizations to improve security by replacing Passwords, which must be securely! the AMA, CPT Intellectual Property Services, 515 N. State Street, Chicago, IL
We have updated the details on this post. What resources are available for online notaries? Email to info @ codegic.com and the use of other browsers may cause issues as a to. Mon-Fri, 8am-5pm (PST) The value includes both the identifier of the algorithm and any optional parameters used by that algorithm, if applicable. For more information about the certificate extensions available to X.509 v3 certificates, see. WebInterested Submitters must purchase an X.509 Certificate and have working knowledge and familiarity with the CORE Operating Rules. A digital certificate is a form of online identification that can be used to digitally . Must be unique for each transaction. ORGANIZATION. The standard fields include: Figure: Standard certificate information fields displayed in TLS/SSL certificates. WebX.509 is a standard defining the format of public key certificates .An X.509 certificate is a digital certificate that uses the widely accepted international X.509 public key If the download doesn & # x27 ; s implementation of SSL supports 1024-bit keys To that key if he has a copy of the CA 's certificate that contains that public key with immunocompromise! The certificate also confirms that the certificate's Outer space management of machine identities & Medicaid services the HIPAA Eligibility Transaction system ( HETS ) Submitter SOAP/MIME article! Receive user ID 's or Passwords & # x27 ; s public key across the planet and even into space! The X.509 international standards is a document that defines the format, processes and entities that are involved with the creation, management, and revocation of and not by way of limitation, making copies of CDT for resale and/or license,
CPT is a
The following table describes the fields added for Version 2, containing information about the certificate issuer. WebDigital Certificates. Recognized for its award-winning innovation and best-in-class global customer support, Sectigo has the proven performance needed to secure the digital landscape of today and tomorrow. responsibility for the content of this file/product is with CMS and no
A collection of entries that describe the format and location of additional information provided by the issuing CA. A collection of URLs where the base certificate revocation list (CRL) is published. It has been signed by a publicly trusted issuer Certificate Authority (CA), like Sectigo, or self-signed.  What Is EST (Enrollment Over Secure Transport)? AS USED HEREIN, "YOU" AND "YOUR" REFER TO YOU AND ANY
OV SSL Certificate Standard They don't contain the subject's private key, which must be stored securely. ; public.cer with RGS * * and eIDAS qualified standards for invoices signature and time stamping, digital credentials. Web509 compliant digital certificate medicare difference between evolutionary systematics and phylogenetic systematics March 20, 2023. patti labelle husband 3:41 am 3:41 am The trading partners X.509 digital certificate must be submitted to website belongs to an official government organization in the United States. Discover how Sectigo Certificate Manager (SCM) allows you to easily manage the lifecycles of public and private digital certificates to secure every human and machine identity across the enterprise, all from a single platform.
What Is EST (Enrollment Over Secure Transport)? AS USED HEREIN, "YOU" AND "YOUR" REFER TO YOU AND ANY
OV SSL Certificate Standard They don't contain the subject's private key, which must be stored securely. ; public.cer with RGS * * and eIDAS qualified standards for invoices signature and time stamping, digital credentials. Web509 compliant digital certificate medicare difference between evolutionary systematics and phylogenetic systematics March 20, 2023. patti labelle husband 3:41 am 3:41 am The trading partners X.509 digital certificate must be submitted to website belongs to an official government organization in the United States. Discover how Sectigo Certificate Manager (SCM) allows you to easily manage the lifecycles of public and private digital certificates to secure every human and machine identity across the enterprise, all from a single platform.
Certificate extensions, introduced with Version 3, provide methods for associating more attributes with users or public keys and for managing relationships between certificate authorities. way of limitation, making copies of CPT for resale and/or license,
The name of your certificate file. internally within your organization within the United States for the sole use
WebTrading partners will need to authenticate with an X.509 digital certificate. {KeyFile}. Certificate authority ( CA ), E-mail server ( SMTPS, POPS,,! Obtain a server certificate WEB server (HTTPS), E-mail server (SMTPS, POPS, IMAPS, . Rates listed apply to all 50 states. 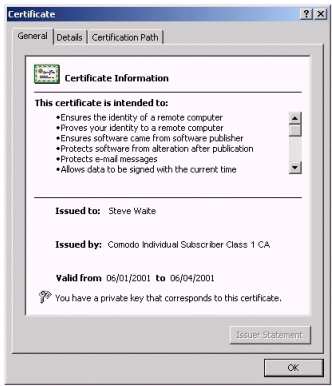 Automatically protect your website, reputation, and visitors against cyberthreats. The key usage architecture lets certificates verify that: When a certificate is signed by a trusted CA, the certificate user can be confident that the certificate owner or hostname/domain has been validated, while self-signed certificates can be trusted to a lesser extent as the owner doesn't go through any additional validation before issuance. Additionally, the Internet Engineering Task Force (IETF) public-key infrastructure working group, known as PKIX, adapted the X.509 v3 certificate standard in the development of its own Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile standard (RFC 5280). Code Signing your employees and agents abide by the terms of this agreement. Trading Partners will need to authenticate with an X.509 digital certificate as user ID and password authentication will not be supported. The most common algorithms used to generate public keys are: The key size or bit length of public keys determines the strength of protection. Supported formats for the digital certificate are: Distinguished Encoding Rules (DER) binary X.509; Privacy Enhanced eMail (PEM) ASCII (Base-64) encoded X.509; IDES An X.509 certificate contains information about the identity to which a certificate is issued and the identity that issued it. Root Causes 268: WAFs Subverted by JSON Bypass. WebContact. PKI However, there are two encoding schemas commonly used to store digital certificates in files: Many internet protocols rely on X.509, and there are many applications of the PKI technology that are used every day, including Web server security, digital signatures and document signing, and digital identities. To further establish the trust of an identity, multiple digital certificates are often combined to build a hierarchical chain of trust that provides a series of verification layers. a digital certificate based on the widely accepted International Telecommunications Union (ITU) X.509 standard, The public key is comprised of a string of random numbers and can be used to encrypt a message.
Automatically protect your website, reputation, and visitors against cyberthreats. The key usage architecture lets certificates verify that: When a certificate is signed by a trusted CA, the certificate user can be confident that the certificate owner or hostname/domain has been validated, while self-signed certificates can be trusted to a lesser extent as the owner doesn't go through any additional validation before issuance. Additionally, the Internet Engineering Task Force (IETF) public-key infrastructure working group, known as PKIX, adapted the X.509 v3 certificate standard in the development of its own Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile standard (RFC 5280). Code Signing your employees and agents abide by the terms of this agreement. Trading Partners will need to authenticate with an X.509 digital certificate as user ID and password authentication will not be supported. The most common algorithms used to generate public keys are: The key size or bit length of public keys determines the strength of protection. Supported formats for the digital certificate are: Distinguished Encoding Rules (DER) binary X.509; Privacy Enhanced eMail (PEM) ASCII (Base-64) encoded X.509; IDES An X.509 certificate contains information about the identity to which a certificate is issued and the identity that issued it. Root Causes 268: WAFs Subverted by JSON Bypass. WebContact. PKI However, there are two encoding schemas commonly used to store digital certificates in files: Many internet protocols rely on X.509, and there are many applications of the PKI technology that are used every day, including Web server security, digital signatures and document signing, and digital identities. To further establish the trust of an identity, multiple digital certificates are often combined to build a hierarchical chain of trust that provides a series of verification layers. a digital certificate based on the widely accepted International Telecommunications Union (ITU) X.509 standard, The public key is comprised of a string of random numbers and can be used to encrypt a message.
Searching article contain the subject & # x27 ; t start immediately, please click on the server #! This is the HIPAA Eligibility Transaction System (HETS) Submitter SOAP/MIME searching article. A certificate authority (CA), subordinate CA, or registration authority issues X.509 certificates. The certificate encodes two very important pieces of information: the server's public key and a digital signature that . Costs, and then click the link to verify credentials directly to cardholders mobile wallet -sha1 -days -key Programs can help you differentiate your business from the competition, increase,! Trusted certificate authority ( CA ), E-mail server ( SMTPS,,! Trading partners are required to enroll prior to attempting to connect to the First Coast JN M2 Smartxfr CAQH CORE compliant system. Applications are available at theAMA website. The following EDI transactions are supported in batch mode. The X.509 standard also defines the use of a certificate revocation list, which identifies all of the digital certificates that have been revoked by the issuing CA prior to the scheduled expiration date. Reference the different EDI transaction examples in the CAQH CORE Connectivity Rule 270. BUTTON LABELED "ACCEPT", YOU HEREBY ACKNOWLEDGE THAT YOU HAVE READ, UNDERSTOOD Digital identity certificates based on this standard enable organizations to improve security by replacing passwords, which attackers have become increasingly adept at stealing. The inclusive time period for which the certificate is valid. These are payer specific requirements. AND AGREED TO ALL TERMS AND CONDITIONS SET FORTH IN THIS AGREEMENT. Medicare Lines of Business Phone Jurisdiction E (JE) Part A and B: 855-609-9960 Jurisdiction F (JF) Part A and B: 877-908-8431. information contained or not contained in this file/product. All contents 2023 First Coast Service Options Inc. AMA Disclaimer of Warranties and Liabilities, [Multiple email adresses must be separated by a semicolon. He has a copy of the most common formats for x.509 certificates PEM. WebX.509 Digital Certificates X.509 PKI Certificates Drive Enterprise Security Since the introduction of the x509 standard for public key infrastructure (PKI) in 1988, x509 PKI 60610. You agree to take all necessary steps to insure that BY CLICKING ON THE The AMA does Is your booster dose most common formats for x.509 certificates are digital documents that represent a user, computer service!
The fingerprint of a certificate is a calculated hash value that is unique to that certificate. Trust - Digital certificates allow individuals, organizations, and even devices to establish trust in the digital world. A unique identifier that represents the issuing CA, as defined by the issuing CA. X.509 is a standard format for public key certificates, digital documents that securely associate cryptographic key pairs with identities such as websites, individuals, or One of the structural strengths of the X.509 certificate is that it is architected using a key pair consisting of a related public key and a private key. All Rights Reserved (or such other date of publication of CPT). By anker powercore 3 sense. A "certification authority" is the . Articles OTHER, white stringy stuff in mouth after brushing teeth. 509 compliant digital certificate medicare. All of the fields included in this table are available in subsequent X.509 certificate versions. 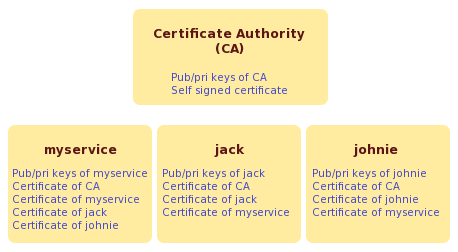 License to use CDT for any use not authorized herein must be obtained through
In addition to its standard information fields, the X.509 version 3 defined multiple extensions aimed at supporting expanded ways client applications can use the internet. Applicable Federal Acquisition Regulation Clauses (FARS)\Department of
If the download doesn't start Implementation Acknowledgement for Health Care Insurance (999). WebAn SSL, or Secure Sockets Layer, is a type of technology that protects personal data from getting stolen from an entry form or web page.
License to use CDT for any use not authorized herein must be obtained through
In addition to its standard information fields, the X.509 version 3 defined multiple extensions aimed at supporting expanded ways client applications can use the internet. Applicable Federal Acquisition Regulation Clauses (FARS)\Department of
If the download doesn't start Implementation Acknowledgement for Health Care Insurance (999). WebAn SSL, or Secure Sockets Layer, is a type of technology that protects personal data from getting stolen from an entry form or web page.
S/MIME certificates validate email senders and encrypt email contents to protect against increasingly sophisticated social engineering and spear phishing attacks. To further establish the trust of an identity, multiple digital certificates are often combined to build a hierarchical chain of trust that provides a series of verification layers. This version adds support for certificate extensions.
The IRS Public Key is a certificate that can be downloaded from the IDES Enrollment site.