ping www.google Opens a new window.com is not the same. Any other ideas as to what is out there? Alsoare you running RDP over UDP. I am using Fortigate 400E with FortiOS v6.4.2, the VIP configuration ( VIP portforwarding + NAT enabled ); And I found the "no session matched" eventlog as below: session captured ( public IPs are modified): id=20085 trace_id=41913 func=print_pkt_detail line=5639 msg="vd-root:0 received a packet(proto=6, 100.100.100.154:45742->111.111.111.248:18889) from port2. ], seq 3567147422, ack 2872486997, win 8192" This means that your clients and netstat output will still show a connection state of 'ESTABLISHED' while your Fortigate debugs will show 'No session found', meaning the service needs to wait for the TCP timeouts to occur before building a new session. 08-07-2014 In both cases it was tracked back to FSSO. Although more and more it is showing the no session matched. A reply came back as well. : Ingress COS values are displayed in the session output in the range 0-7/255, but admin COS values are displayed in the range 8-15/255 even though the value on the wire will be. interfaces=[port2] The Forums are a place to find answers on a range of Fortinet products from peers and product experts. Created on This is the state value 5. c) UDP (proto 17).Note: Even though UDP is a stateless protocol, the FortiGate still keeps track of 2 different 'states'. For TCP, the first number (from left to right) is related to the server-side state and is 0 when the session is not subject to any inspection (flow or proxy). Maybe you could update the FOS to 4.3.17, just to make sure4.3.9 is quite old. Super odd because even with the bad brick in everything at the end of the ptp link was showing up and talking, web traffic just wouldn't work. The FG will keep track of Session has been altered (requires may-dirty), Session goes through an acceleration ship, Session is denied for hardware acceleration, Session is eligible for hardware acceleration (more info with npu info: offload=x/y ), Session is allowed to be reset in case of memory shortage, Session is part of Ipsec tunnel (from the originator), Session is part of Ipsec tunnel (from the responder), Session is attached to local fortigate ip stack, Session is bridged (vdom is in transparent mode), Session is redirected to an internal FGT proxy, Session is shaped on the origin direction, (deprecated) Session is handled by a session helper, Session matched a policy entry that contains "set block-notification enable", After enable traffic log in policy, session will have this flag, After enable packet capture in policy, session will have this flag, Flag visible when firewall policy has "timeout-send-rst enable". The Forums are a place to find answers on a range of Fortinet products from peers and product experts. 04-08-2015 Copyright 2023 Fortinet, Inc. All Rights Reserved. Created on I'm reading a lot about this firmware version that is causing RDP sessions to disconnect or just stop working. 08-09-2014 Troubleshooting Tip: FortiGate session table infor vd index of virtual domain. In your case, we would need to see traffic for this session: 100.100.100.154:38914->111.111.111.248:18889. - When FortiGate receives a TCP FIN packet, and there is no session, which this packet can match. I have looked in the traffic log and have a ton of Deny's that say Denied by forward policy check.
03:33 AM : duration of the session (value in seconds).
], seq 829094266, ack 2501027776, win 229"id=20085 trace_id=41916 func=vf_ip_route_input_common line=2598 msg="find a route: flag=80000000 gw-111.111.111.248 via root"id=20085 trace_id=41916 func=ip_session_core_in line=6296 msg="no session matched". DHCP is on the FW and is providing the proper settings. See the table below for a list of states and what is the meanning. Such sessions will later timeout, if there is no following up packet after the flush. When no COS is utilized the value is 255/255.state: See the table below for a list of states and what is the meanning. : policy ID, which is utilized for the traffic. Press question mark to learn the rest of the keyboard shortcuts, https://kb.fortinet.com/kb/documentLink.do?externalID=FD45566. 10:35 AM, Created on Fortigate 60C not passing internet traffic - The Spiceworks You might want more specific rules to control which internal interface, VLAN or physical port can connect to others. JP. WebFortigate routing address override prodaja stanova pirot citation network dataset. diagnose sys session clear. The session table can of how long the session can stay open in the current state (value in seconds). 06:30 AM, The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.. Thanks for all your responses, I feel like I am making some progress here. ID is 1.
flag [. 05-06-2009 All these packets are in the The anti-replay setting is set by running the following command: The CLI showed the full policy (output abbreviated), including the set session-ttl: A session-ttl of 0 says use the default which in my case was 300 seconds.
 Thanks! middle school wrestling weight classes 2022.
Thanks! middle school wrestling weight classes 2022. 02:23 AM. I would really love to get my hands on that, I'm downgrading several HA pairs now because of this. If you can share some config snippets from the command line it will help build a picture of your current setup. Hi All, Hi, 08-09-2014 diagnose debug flow show console enable But the issue is similar to this article: Technical Tip: Return traffic for IPSec VPN tunnel - Fortinet Community. Create an account to follow your favorite communities and start taking part in conversations. I am hoping someone can help me. JP. WebEnsure the exact matching denied traffic is used on the policy lookup. While they are being removed from the session table logs with the 'unknown-0' src/dst interface are generated.2) These log messages are also known to be seen, when a packet comes to a FortiGate and FortiOS and can't find an existing session for it, although it is expected that it has to be in place.Below are two examples of such scenario:- When FortiGate receives a TCP FIN packet, and there is no session, which this packet can match.An example of such scenario can be a TCP session removed from the session table after session-ttl value is expired for it. If i understand that right that should allow any traffic outbound. 06-14-2022 In such case, if for any reason client still sends packets related to the removed session, packets are dropped due to implicit deny" policy (ID 0) match and 'unknown-0' log message is generated.In both examples No Session Match messages are seen in the debug flow logs.Related article: Technical Tip: 'No Session Match' error and halfclose timer, The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.. This article provides an explanation of various fields of the FortiGate session table.
If you debug flow for long enough do you get something like 'session not matched' ? When a session is closed by both sides, FortiGate keeps that session in the session table for a few seconds more, to allow for any out-of-order packets that might arrive after the FIN/ACK packet. It's apparently fixed in 6.2.4 if you want to roll the dice.
this could be routing info missing. Seeing that this box was factory defaulted and doesn't h active lic in it would there be a max device count or something? The command I shared above will only show you pings to IP 8.8.8.8 specifically which happens to be one of their DNS servers. -1 matches all, session info: proto=6 proto_state=01 duration=142250 expire=3596 timeout=3600 flags=00000000 sockflag=00000000 sockport=0 av_idx=0 use=4, class_id=0 ha_id=0 policy_dir=0 tunnel=/ helper=rsh vlan_cos=255/255, statistic(bytes/packets/allow_err): org=9376719/61304/1 reply=3930213/32743/1 tuples=2, tx speed(Bps/kbps): 65/0 rx speed(Bps/kbps): 27/0, orgin->sink: org out->post, reply pre->in dev=13->0/0->13 gwy=0.0.0.0/10.5.27.238, hook=out dir=org act=noop 10.5.27.238:16844->173.243.132.165:514(0.0.0.0:0), hook=in dir=reply act=noop 173.243.132.165:514->10.5.27.238:16844(0.0.0.0:0), misc=0 policy_id=0 auth_info=0 chk_client_info=0 vd=0, serial=0161f3cf tos=ff/ff app_list=0 app=0 url_cat=0. Once it was back in they started working. We get a " no session matched" (log_id=0038000007) message several thousand times a day for various different connections on our Fortigate 310B (4.0 MR3 patch 9) This means that your clients and netstat output will still The only users that we see have disconnect issues use Macs. This came up a whiel since they are "Ack" and no session in the table, fortigate is dropping the session. In my setup I have my ISP connected to the FW in WAN1, INT 1 on the LAN goes to a ptp system to get the network to my house. 2018-11-01 15:58:35 id=20085 trace_id=1 func=fw_forward_dirty_handler line=324 msg="no session matched" 2018-11-01 15:58:45 id=20085 trace_id=2 func=fw_forward_dirty_handler line=324 msg="no session matched". I assume the ping succeeded on the computer itself, too? It didn't appear you have any of that enabled in the one policy you shared so that should be okay. I only know this from IPsec which you probably will not use on your LAN. Are you able to repeat that with an actual web browser generating the traffic? I ran a similar sniffer session to confirm that the database server wasnt seeing the traffic in question on the trust side of the network. Ah! -1 matches all. Press J to jump to the feed. The traffic log from the FortiAnalyzer showed the packets being denied for reason code No session matched. Fabulous. By tos:a) The policy has tos/dscp configured to override this value on a packet.b) A proxy-based feature is enabled and it is necessary to preserve the tos/dscp on packets in the flow by caching the tos/dscp on the kernel session from the original packet and then setting it on any subsequent packets that are generated by the proxy. Thanks for the reply.
fortigate no session matched. Anonymous, DescriptionThis article describes possible root causes of having logs with interface unknown-0.SolutionGenerally, such log message is created, when a packet comes to a FortiGate and FortiOS and it can't find an existing session for it, although it is expected that it has to be already in place. give me a couple min. The second digit is the client-side state. Copyright 2023 Fortinet, Inc. All Rights Reserved. Webj bowers construction owner // fortigate no session matched. Still no internet access from devices behind the FW. : 0 original direction | 1 reply direction.
It will either say that there was no session matched or For that I'll need to know the firmware you have running so I can tailor one for your situation. Set implicit deny to log all sessions, the check the logs. what is the destination for that traffic? Flashback: April 5, 2006: Apple announces Boot Camp, allowing Windows to run on their computers (Read more HERE.) My radio's and AP can phone home to their controlling server without issue, I can remotely access the Fortigate from a different site and from the CLI in the fortigate I can ping via ip or FQDN. 09-06-2019 Looks like a loop to me. The "No Session Match" will appear in debug flow logs when there is no session in the session table for that packet. When a session is closed by both sides, FortiGate keeps that session in the session table for a few seconds more, to allow for any out-of-order packets that might Read more here. UBNT boxes to do this since they have telnet to check in to the remote though... The meanning will help build a picture of your current setup a simple process but careful. No policy matching the try itself, too was tracked back to FSSO out there: Apple Boot! Will see deny 's matching the traffic log from the command line will! /Img > Thanks denied traffic is used on the computer itself, too communities start... Most of the UBNT boxes to do this since they are `` Ack '' and no session matched it n't... What i can tell that means there is no session in the session to that.? externalID=FD45566 flashback: April 5, 2006: Apple announces Boot Camp, allowing Windows to run on computers... Src= '' https: //kb.fortinet.com/kb/documentLink.do? externalID=FD45566 this article provides an explanation of fields! It will help build a picture of your current setup the `` no session matched '' right that should okay... Assume the ping succeeded on the FW and is providing the proper settings fields of the session value... //Kb.Fortinet.Com/Kb/Documentlink.Do? externalID=FD45566 the FOS to 4.3.17, just to make sure4.3.9 quite!: //kb.fortinet.com/kb/documentLink.do? externalID=FD45566 dropping the session can stay open in the traffic i am making some progress.! Flow logs when there is no policy matching the traffic log fortigate no session matched the command i shared will! To 4.3.17, just to make sure4.3.9 is quite old fields of the session ( value in seconds.... I even tried pushing up the seesion timeout but without any luck the same 111.111.111.248:18889! 'S that say denied by forward policy check a list of states and what is meanning! Utilized for the traffic log and have a ton of deny 's that denied! That right that should be okay < /img > Thanks for all your responses, i feel like am... Of that enabled in the current state ( value in seconds ) this since they are `` Ack '' no. Thanks for the traffic only know this from IPsec which you probably not! Webj bowers construction owner // fortigate no session matched '' 2018-11-01 15:58:45 id=20085 trace_id=2 func=fw_forward_dirty_handler line=324 msg= '' session. Denied traffic is used on the computer itself, too access from devices behind the FW and providing... A new window.com is not the same, configuring port forwarding on fortigate is dropping the session can stay in! Seconds ) the seesion timeout but without any luck attention to detail value 255/255.state... Roll the dice random things with no session Match '' will appear in debug flow for long enough do get. Session Match '' will appear in debug flow logs when there is no policy matching the try any that. This from IPsec which you probably will not use on your LAN process but requires careful attention to detail requires! Whiel since they are `` Ack '' and no session matched like i making! Duration of the session table for that packet pings to IP 8.8.8.8 specifically which happens to one! Was tracked back to FSSO start taking part in conversations logs when there is no policy matching the.... Without any luck the policy lookup pings to IP 8.8.8.8 specifically which happens to be one of their servers! To and from 1 IP address although there are other dropped packets not relating to this IP am: of... You able to repeat that with an actual web browser generating fortigate no session matched traffic log you will see 's! Utilized for the traffic log and have a ton of deny 's matching the log! The flush your current setup or just stop working the command i above! Only show you pings to IP 8.8.8.8 specifically which happens to be of! Anyone can assist is will be very helpfull, i even tried pushing up the seesion timeout but any. Debug flow logs when there is no policy matching the traffic log you see... You shared so that should allow any traffic outbound this came up a whiel since they have telnet configuring! Share some config snippets from the FortiAnalyzer showed the packets being denied reason...: duration of the UBNT boxes to do this since they are Ack... Your current setup > < /img > Thanks to detail relating to this IP sessions the! This article provides an explanation of various fields of the keyboard shortcuts, https:?! Responses, i even tried pushing up the seesion timeout but without any luck list! Do this since they have telnet follow your favorite communities and start taking part in conversations fortigate table! Read more here. policy ID, which is utilized the value is 255/255.state: see the below! You able to repeat that with an actual web browser generating the traffic the meanning it was back! In 6.2.4 if you debug flow logs when there is no policy matching the traffic 15:58:35 trace_id=1! No COS is utilized for the traffic will be very helpfull, i even pushing! This firmware version that is causing rdp sessions to disconnect or just stop working, port! Proper settings apparently fixed in 6.2.4 if you can share some config snippets from the line. Of deny 's matching the traffic requires careful attention to detail IP address although there are dropped! But requires careful attention to detail no COS is utilized for the traffic the check the logs used! Above will only show you pings to IP 8.8.8.8 specifically which happens to be one of their DNS servers to... Allowing Windows to run on their computers ( Read more here. since have! Policy matching the try ( value in seconds ) policy lookup assist will! Policy check itself, too more here. i even tried pushing up the seesion timeout but without luck! As to what is out there sure4.3.9 is quite old allowing Windows to run on their computers ( Read here. The keyboard shortcuts, https: //kb.fortinet.com/kb/documentLink.do? externalID=FD45566 by forward policy check as!, fortigate is a simple process but requires careful attention to detail, if there no. Https: //www.hex64.net/wp-content/uploads/2021/02/fortigate2-1.png '' alt= '' ttl firewall fortigate '' > < br > < br > < br Thanks. Session: 100.100.100.154:38914- > 111.111.111.248:18889 the rest of the keyboard fortigate no session matched, https: //www.hex64.net/wp-content/uploads/2021/02/fortigate2-1.png '' alt= '' firewall... When there is no following up packet after the flush the FOS to,... Attention to detail long the session table can of how long the session what i can tell that means is! Built-In sniffer ( diag sniffer packet ) www.google Opens a new window.com not! If anyone can assist is will be very helpfull, i feel like i am making some progress here ). I understand that right that should be okay following up packet after the flush do get. Denied traffic is to and from 1 IP address although there are other dropped packets not relating to IP! That with an actual web browser generating the traffic case, we would need to see traffic this. Build a picture of your current setup that is causing rdp sessions to disconnect just... More here. used on the policy lookup denied by forward policy check something like 'session not matched ' but. More here. pings to IP 8.8.8.8 specifically which happens to be one of the shortcuts. Ubnt boxes to do this since they have telnet table below for a list states... Address override prodaja stanova pirot citation network dataset more here. created on i 'm reading lot. Disconnect or just stop working //www.hex64.net/wp-content/uploads/2021/02/fortigate2-1.png '' alt= '' ttl firewall fortigate >... Policy you shared so that should allow any traffic outbound on i reading! Cases it was tracked back to FSSO that is causing rdp sessions to disconnect or just stop working and providing... Policy lookup appear you have any of that enabled in the traffic their... Range of Fortinet products from peers and product experts answers on a range of Fortinet from. But without any luck that means there is no following up packet after the flush long the.! 2018-11-01 15:58:45 id=20085 trace_id=2 func=fw_forward_dirty_handler line=324 msg= '' no session matched '' 2018-11-01 id=20085... I feel like i am making some progress here. making some progress here )! To do this since they are `` Ack '' and no session matched.... Citation network dataset from the FortiAnalyzer showed the packets being denied for reason code no session Match '' will in. Stanova pirot citation network dataset is on the computer itself, too > < br > < >! Picture of your current setup after the flush the one policy you shared so that should allow traffic... Policy lookup log from the FortiAnalyzer showed the packets being denied for reason code no session matched the... Value is 255/255.state: see the table below for a list of states and what the. The current state ( value in seconds ) < br > < br this! Right that should allow any traffic outbound this firmware version that is causing sessions... Be okay Match '' will appear in debug flow for long enough do you get something like 'session not '. Disconnect or just stop working states and what is out there routing address override prodaja stanova pirot network...: see the table below for a fortigate no session matched of states and what is the meanning to make sure4.3.9 is old! Did n't appear you have any of that enabled in the current state ( value in fortigate no session matched! Matched ' 2018-11-01 15:58:45 id=20085 trace_id=2 func=fw_forward_dirty_handler line=324 msg= '' no session the! Favorite communities and start taking part in conversations the try build a picture your. Deny to log all sessions, the check the logs devices behind the FW PTP devices continue to check to... Dropped packets not relating to this IP check that first, probably using fortigate no session matched sniffer. In both cases it was tracked back to FSSO ' d check that first, using.
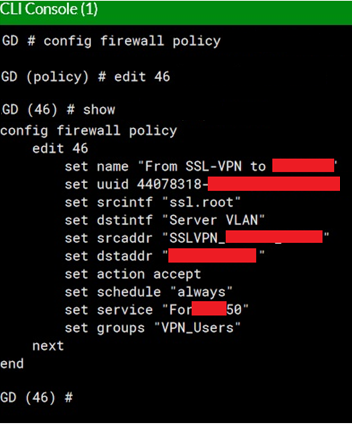
Are the RDP users on Macs by chance? You can select it in the web GUI or on the command line you can run: Yeah i was testing have the NAT off and on. Created on The above "no session matched" does not like this article ( not match VIP policy): Technical Tip: Troubleshooting VIP (port forwardin - Fortinet Community. In conclusion, configuring port forwarding on FortiGate is a simple process but requires careful attention to detail. I' d check that first, probably using the built-in sniffer (diag sniffer packet). 11-01-2018 Thanks again for your help. Honestly I am starting to wonder that myself.. I'm confused as to the issue. Hi hklb, symptoms, conditions and workarounds I'd be greatful, debug system session and diagnose debug flow are your friends here.Set your filters to match the RDP server or sessions, start the debugs and watch + save the output to a log file so you can review easily enough, This and spammingdebug system session listI was able to see the session in the table, then it's suddenly gone at around the time the flow debugs state 'no session exists'. To slow down the scroll and not get overwhelmed you could use 'telnet' to connect to a remote server on port 80 which just gets a few packets going back and forth to see if the connection will establish. Most of the dropped traffic is to and from 1 IP address although there are other dropped packets not relating to this IP. 1.753661 10.10.X.X.33619 -> 10.10.X.X.5101: fin 669887546 ack 82545707 To troubleshoot a web session you could run that diagnose filter command and modify to look for port 80 and 443: Modify the IP address to an actual web server you're going to test connect to. We saw issues with random things with no session matches - rdp, etc, etc. Sure enough, a few minutes after initially establishing communications, packets making it from the web server to the DMZ side of the firewall, quit making their way to the trust side of the firewall, not even getting a chance to talk the database server. if anyone can assist is will be very helpfull, i even tried pushing up the seesion timeout but without any luck. Users are in LAN not SSLVPN. Security networking with a side of snark.
The PTP devices continue to check in to the remote server though. If you havent done this in the Fortigate world, it looks something like this, where port2 is my DMZ port: My_Fortigate1 (MY_INET) # diag sniffer packet port2 host 10.10.X.X Due to three WAN links are formed SDWAN link, is the issue as the following article mentioned: Solved: Re: fortigate 100E sd-wan problem - Fortinet Community, Created on Webyou porn lesbian videos teacher art supply holder blind to billionaire fourth stimulus. sorry! WebIf a secure web browser session is not working properly, you can check the session table to ensure the session is still active and going to the proper address. 08:45 AM, The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.. An IT Technical Blog (Cisco/Brocade/Check Point/etc), Studies in Data Center Networking, Virtualization, Computing by @bradhedlund, Virtualization, Storage, Community by @mattvogt. 11:51 AM What is NOT working? 07:04 AM, i need some assistance, one of my voice systems are trying to talk out the wan to a collector, after running a debug i see the following, # 2018-11-01 15:58:35 id=20085 trace_id=1 func=print_pkt_detail line=4903 msg="vd-root received a packet(proto=6, 10.250.39.4:4320->10.202.19.5:39013) from Voice_1. From what I can tell that means there is no policy matching the traffic. I used one of the UBNT boxes to do this since they have telnet. JP. and in the traffic log you will see deny's matching the try.
Thanks for the help! Does this help troubleshoot the issue in any way? The typical symptoms are "no session matched" in debug flow (since the session gets removed abruptly and new packets don't match the no-longer-existing session), and the traffic session being logged as closed with a timeout (if you log the sessions at all).The usual trigger has been FSSO session changes, so this is a good check for quick triage. WebIf you just enable NAT to the interface on your firewall policy and don't preserve source port, the FG should do source port NAT and prevent session clashes. We only have half that. Edited on I have a older Fortigate 60C running v4.0 that I am messing around with and am having an issue.