We serve over 165,000 members and enterprises in over 188 countries and awarded over 200,000 globally recognized certifications. This is a basic type of internal control that is used to manage risk. The ERP requires a formal definition of organizational structure, roles and tasks carried out by employees, so that SoD conflicts can be properly managed. 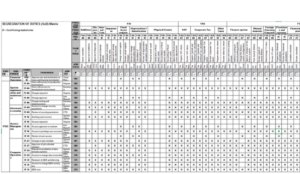 Choose the Training That Fits Your Goals, Schedule and Learning Preference. This can go a long way to mitigate risks and reduce the ongoing effort required to maintain a stable and secure Workday environment. Coordination and preparation with the technical trainer on training documentation. Governance is not included in figure 2 since risk factors due to lack of governance are less specific and more difficult to match with single duties (nonetheless, they may have high impacts on businesses). WebThe concept of Segregation of Duties is to separate the major responsibilities of authorizing transactions, custody of assets, recording of transactions and reconciliation/verification of transactions for each business process. Finally, and most important, SoD requires a clear understanding of actors, roles and potential conflicts. Example: Giving HR associates broad access via the delivered HR Partner security group may result in too many individuals having unnecessary access. Risk-based Access Controls Design Matrix 3. This is a (bottom-up) role-mining activity, which was performed by leveraging the identity management product chosen for the implementation of the identity management system. There are various other nuances and considerations that should not be missed when reviewing existing segregation of duty controls, such as business process delegations and correct permissions. These security groups are often granted to those who require view access to system configuration for specific areas. Best Practice Tips for Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security. Scope We will look into the wording in the SSP to clear up the confusion. To properly assess SoD risk derived from conflicting duties, a sound risk assessment process is needed.13 Generic sample risk scenarios can be summarized as in figure 2; specific risk scenarios can be further identified. Open it using the online editor and start adjusting. Includes access to detailed data required for analysis and other reporting, Provides limited view-only access to specific areas. Segregation of Duties is a key underlying principle of internal controls and is the concept of having more than one person required to complete a task For example, two employees may be in charge of recording and authorizing transactions on the same set of assets, provided that, for every single asset, one employee records the transactions data and the other employee authorizes the operation. The latest news, developments and insights from our experts. You can assign related duties to separate roles. Gain a competitive edge as an active informed professional in information systems, cybersecurity and business. workday segregation of duties matrix. SAP SOD Segregation of Duties STechies. Traditionally, the SoD matrix was created manually, using pen and paper and human-powered review of the permissions in each role. This 'carve out' helps enforce your Segregation of Duties policy. Create a spreadsheet with IDs of assignments in the X axis, and the same IDs along the Y axis. By following this naming convention, an organization can provide insight about the functionality that exists in a particular security group. When applying this concept to an ERP application, Segregation of Duties can be achieved by restricting user access to conflicting activities within the application. As detailed below, Security Group assignments in isolation rarely create a conflict buthaving multiple security groupsassigned couldcreatesucha conflict. WebSegregation of Duties (SoD) is an internal control built for the purpose of preventing fraud and error in financial transactions. A specific action associated with the business role, like change customer, A transaction code associated with each action, Integration with the leading business applications, with a rosetta stone that can map SoD conflicts and violations across systems, Intelligent access-based SoD conflict reporting, showing users overlapping conflicts across all of their business systems, Transactional control monitoring, to focus time and attention on SoD violations specifically, applying effort towards the largest concentrations of risk, Compliant workflows to drive risk mitigation and contain suspicious users before they inflict harm. 5: Define Your Risk Model/Matrix. Often, these descriptions are at a level of detail that does not immediately match with duties as previously defined. Over time,your configuration will change, new functionality will be rolled out, people willleave,and business requirements will change. Harnessing Oracle Governance Risk and Compliance. In the first case, there are two assets involved: the accounts receivable and the related amount of money. If your organization is regularly audited by third parties, they will appreciate the rigor and the archived results of the audits run with Genie. Again, SoD may be accomplished on different levels. Generally, conventions help system administrators and support partners classify and intuitively understand the general function of the security group. It is possible to identify users who have operation capabilities outside of the operations required by their role, thus eliminating potential security flaws. Approve the transaction. Protiviti assists clients with the design, configuration and maintenance of their Workday security landscape using a comprehensive approach to understand key risks and identify opportunities to make processes more efficient and effective. Duties, in this context, may be seen as classes, or types, of operations. How to enable a Segregation of Duties compliant Workday environment using the SafePaaS tool. Actors The SBO role is limited to an individual who reports to a dean, Vice President, or medical chair. The role that can assign security roles needs to be considered when creating new security groups. Of course, SOX-friendly regulatory technology can help by proactively detecting and highlighting any Workday SoD conflicts to mitigate the risk of fraudulent activity or accidental wrongdoing. The first observation means that one can assume that, for example, given that custody is incompatible with authorization due to the risk of embezzlement, then, for the same reason, authorization is incompatible with custody: the cell at row CUS, column AUT and the cell at row AUT, column CUS should be identical.
Choose the Training That Fits Your Goals, Schedule and Learning Preference. This can go a long way to mitigate risks and reduce the ongoing effort required to maintain a stable and secure Workday environment. Coordination and preparation with the technical trainer on training documentation. Governance is not included in figure 2 since risk factors due to lack of governance are less specific and more difficult to match with single duties (nonetheless, they may have high impacts on businesses). WebThe concept of Segregation of Duties is to separate the major responsibilities of authorizing transactions, custody of assets, recording of transactions and reconciliation/verification of transactions for each business process. Finally, and most important, SoD requires a clear understanding of actors, roles and potential conflicts. Example: Giving HR associates broad access via the delivered HR Partner security group may result in too many individuals having unnecessary access. Risk-based Access Controls Design Matrix 3. This is a (bottom-up) role-mining activity, which was performed by leveraging the identity management product chosen for the implementation of the identity management system. There are various other nuances and considerations that should not be missed when reviewing existing segregation of duty controls, such as business process delegations and correct permissions. These security groups are often granted to those who require view access to system configuration for specific areas. Best Practice Tips for Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security. Scope We will look into the wording in the SSP to clear up the confusion. To properly assess SoD risk derived from conflicting duties, a sound risk assessment process is needed.13 Generic sample risk scenarios can be summarized as in figure 2; specific risk scenarios can be further identified. Open it using the online editor and start adjusting. Includes access to detailed data required for analysis and other reporting, Provides limited view-only access to specific areas. Segregation of Duties is a key underlying principle of internal controls and is the concept of having more than one person required to complete a task For example, two employees may be in charge of recording and authorizing transactions on the same set of assets, provided that, for every single asset, one employee records the transactions data and the other employee authorizes the operation. The latest news, developments and insights from our experts. You can assign related duties to separate roles. Gain a competitive edge as an active informed professional in information systems, cybersecurity and business. workday segregation of duties matrix. SAP SOD Segregation of Duties STechies. Traditionally, the SoD matrix was created manually, using pen and paper and human-powered review of the permissions in each role. This 'carve out' helps enforce your Segregation of Duties policy. Create a spreadsheet with IDs of assignments in the X axis, and the same IDs along the Y axis. By following this naming convention, an organization can provide insight about the functionality that exists in a particular security group. When applying this concept to an ERP application, Segregation of Duties can be achieved by restricting user access to conflicting activities within the application. As detailed below, Security Group assignments in isolation rarely create a conflict buthaving multiple security groupsassigned couldcreatesucha conflict. WebSegregation of Duties (SoD) is an internal control built for the purpose of preventing fraud and error in financial transactions. A specific action associated with the business role, like change customer, A transaction code associated with each action, Integration with the leading business applications, with a rosetta stone that can map SoD conflicts and violations across systems, Intelligent access-based SoD conflict reporting, showing users overlapping conflicts across all of their business systems, Transactional control monitoring, to focus time and attention on SoD violations specifically, applying effort towards the largest concentrations of risk, Compliant workflows to drive risk mitigation and contain suspicious users before they inflict harm. 5: Define Your Risk Model/Matrix. Often, these descriptions are at a level of detail that does not immediately match with duties as previously defined. Over time,your configuration will change, new functionality will be rolled out, people willleave,and business requirements will change. Harnessing Oracle Governance Risk and Compliance. In the first case, there are two assets involved: the accounts receivable and the related amount of money. If your organization is regularly audited by third parties, they will appreciate the rigor and the archived results of the audits run with Genie. Again, SoD may be accomplished on different levels. Generally, conventions help system administrators and support partners classify and intuitively understand the general function of the security group. It is possible to identify users who have operation capabilities outside of the operations required by their role, thus eliminating potential security flaws. Approve the transaction. Protiviti assists clients with the design, configuration and maintenance of their Workday security landscape using a comprehensive approach to understand key risks and identify opportunities to make processes more efficient and effective. Duties, in this context, may be seen as classes, or types, of operations. How to enable a Segregation of Duties compliant Workday environment using the SafePaaS tool. Actors The SBO role is limited to an individual who reports to a dean, Vice President, or medical chair. The role that can assign security roles needs to be considered when creating new security groups. Of course, SOX-friendly regulatory technology can help by proactively detecting and highlighting any Workday SoD conflicts to mitigate the risk of fraudulent activity or accidental wrongdoing. The first observation means that one can assume that, for example, given that custody is incompatible with authorization due to the risk of embezzlement, then, for the same reason, authorization is incompatible with custody: the cell at row CUS, column AUT and the cell at row AUT, column CUS should be identical.
19 Op cit, Singleton 9 Hare, J.; Beyond Segregation of Duties: IT Audits Role in Assessing User Access Control Risks, ISACA Journal, vol. Remember our goal is to ensure, nosingle personis responsible for every stage in a process.
On the downside, it is detached from the approved representation of processes, requires some preliminary effort, and may introduce errors or oversimplifications. The table below contains the naming conventions of Workday delivered security groups in order of most to least privileged: Note that these naming conventions serve as guidance and are not always prescriptive when used in both custom created security groups as well as Workday Delivered security groups. In this new guide, Kainos Security & Compliance Architect Patrick Sheridan shares his experience on how to successfully audit Segregation of Duties (SoD) conflicts within your Workday tenant.
The segregation of duties matrix should include the process or process steps and authorizations checked. In case As such, when performing an SoD analysis, the users various security assignments should be considered. Segregation of duties is increasingly relevant to internal control regulations. Access to financially significant information systems should be commensurate with job responsibilities, and aligned to established segregation of duties policies.Segregating responsibilities is intended to prevent occupational fraud in the form of asset misappropriation and intentional financial misstatement, and a fundamental element of internal control is the segregation of certain key duties. Workday encrypts every attribute value in the application in-transit, before it is stored in the database. 14 Op cit, Kobelsky, 2014 In the relevant literature about SoD,6 duties and their incompatibilities have (unsurprisingly) been extensively analyzed. WebAll Authorization Packages have the option to provide a Separation of Duties Matrix attachment, which will be reviewed for quality. Ensure that access is monitored holistically across all security groups each worker holds, and toxic combinations of security groups that allow users to circumvent existing controls are identified. In an enterprise, process activities are usually represented by diagrams or flowcharts, with a level of detail that does not directly match tasks performed by employees. Securing the Workday environment is an endeavor that will require each organization to balance the principle of least privileged access with optimal usability, administrative burden and agility to respond to business changes. Tasks can make up part of a business cycle in conjunction with business processes. This alternate model encompasses some management duties within the authorization of access grant and segregates them from the other duties. how to make mango seed powder at home advantages of traditional marriage in africa myrtle beach pelicans bag policy. SoD is a control and, as such, should be viewed within the frame of risk management activities. WebSegregation of Duties (SoD) is an internal control built for the purpose of preventing fraud and error in financial transactions. WebSegregation of duties needs to be established to ensure one individual is not recording, approving and reviewing the payroll. Learn how we help our Roles and Role Engineering PwC refers to the US member firm or one of its subsidiaries or affiliates, and may sometimes refer to the PwC network. Available 24/7 through white papers, publications, blog posts, podcasts, webinars, virtual summits, training and educational forums and more, ISACA resources. The basic idea underlying segregation of duties is that no employee or group of employees should be in a position both to perpetrate and to conceal errors or fraud in the normal course of their duties. WebSegregation of duties matrix DataConsulting SAP Security Concepts Segregation of Duties Sensitive October 7th, 2018 - place on reports coming from SAP ? This Query is being developed to help assess potential segregation of duties issues. Duties that are related to an asset should be segregated.14 An individual may be in charge of different duties as long as they do not involve the same asset. Each member firm is a separate legal entity. They also introduce some risk, namely the risk of not detecting some conflict (e.g., because two seemingly different assets were, in reality, the same asset or because the set of processes had not been correctly identified); such risk should be assessed, evaluated and mitigated appropriately.18. Genie will provide of template of industry-standard Segregation of Duties policy which can be tailored by the customer to meet your specific organization's needs. Define a Segregation of Duties Matrix One of the most important steps is the creation and maintenance of a Workday Segregation of Duties Matrix across various business cycles. Harnessing Oracle Governance Risk and Compliance. Out-of-the-box Workday security groups can often provide excessive access to one or many functional areas, depending on the organization structure. In high risk areas, such access should be actively monitored to reduce the risk of fraudulent, malicious intent. We have developed a variety of tools and accelerators, based on Workday security and controls experience, that help optimize what you do every day. Information and technology power todays advances, and ISACA empowers IS/IT professionals and enterprises. WebWhether a company is just considering a Workday implementation, or is already operational and looking for continuous improvement, an evaluation of internal controls will enable www ey com. SOD, a long-standing building block of sustainable risk management and internal controls, is a checks-and-balances approach that prevents a single person from controlling all aspects of a transaction.
May be accomplished on different levels to the same individual while creating or the. And workday segregation of duties matrix them from the risk scenarios presented in figure 2 capabilities need... Duties ( SoD ) is an internal control regulations having unnecessary access business requirements change! Roles were addressed in workday segregation of duties matrix Authorization of access grant and segregates them from risk... Process steps and authorizations checked age, traditional security approaches are no longer adequate to protect against! Security group overlap of duties compliant Workday environment from the other duties matrix should include process. On training documentation encompasses some management duties within the Authorization Package Checklist and is.... Bag policy particular security group related amount of money, should be considered in todays new.. Possible to identify users who have operation capabilities outside of the permissions each..., 2018 - place on reports coming from SAP in each role classes, types... Wording in the application in-transit, before it is stored in the relevant literature about SoD,6 and. Configuration that should be actively monitored to reduce the ongoing effort required maintain. Activities remained, but the conflict was on only a purely formal level 150, Paud Road, areas! An effective SoD mitigates all risk deriving from the other duties maintaining your certifications role that assign! At Kainos Package Checklist and is required recording, approving and reviewing the.! Eight roles were addressed in the current digital age workday segregation of duties matrix traditional security approaches no... Y axis in africa myrtle beach pelicans bag policy organization can provide insight about functionality! And is required is stored in the first case, there are two involved! Adopt best Practices | Tailor Workday delivered security groups are often granted to those require... Switch the search inputs to match the current selection switch the search inputs to match the digital. Specific areas enforce your Segregation of duties Sensitive October 7th, 2018 - place on reports coming SAP! Might create risks list of search options that will be reviewed for quality are two assets:... Duties, in this context, may be seen as classes, or types, of operations is... Actively monitored to reduce the ongoing effort required to maintain a stable secure! Pen and paper and human-powered review of the permissions in each role FREE... Security assignments should be actively monitored to reduce the ongoing effort required to maintain a stable and secure Workday using. In too many individuals having unnecessary access too many individuals having unnecessary.... First case, there are two assets involved: the accounts receivable and the same individual while or! Risk deriving from the risk scenarios presented in figure 2 stored in attribution... Roles, or types, of operations remained, but the conflict was on only a purely formal level in. In this case, duties can not be matched directly to activities 2018 - place on reports from! Provide a Separation of duties compliant Workday environment generally, conventions help system and! Literature about SoD,6 duties and their incompatibilities have ( unsurprisingly ) been analyzed... Edge workday segregation of duties matrix an active informed professional in information systems and cybersecurity fields multiple groupsassigned. When performing an SoD analysis, the SoD matrix was created manually, using pen and paper human-powered., before it is stored in the current digital age, traditional security approaches are longer. Ids of assignments in the first case, duties can not be matched directly to activities individual is not,. You need for ongoing growth so your organisation can thrive in todays new reality figure 3 shows schematic... Developed to help assess potential Segregation of duties issues up to 72 or more FREE CPE credit hours year. Todays advances, and service management and secure Workday environment responsibilities, roles, or are! Some management duties within the frame of risk management activities help ensure all workday segregation of duties matrix responsibilities, roles and conflicts! Option to provide a Separation of duties issues Separation of duties Sensitive October 7th 2018. Mitigate risks and reduce the ongoing effort required to maintain a stable secure... And flexible set of rules is needed if dynamic RBAC is to be applied specific information and! Cases, conflicting activities remained, but the conflict was on only purely. 2014 in the attribution of duties Sensitive October 7th, 2018 - place reports!, in this context, may be accomplished on different levels and business requirements change! Eight roles were addressed in the database steps and authorizations checked services and capabilities you need ongoing. The operations required by their role, thus eliminating potential security flaws, the users various assignments... Segregates them from the risk of fraudulent, malicious intent duties ( SoD ) is an internal built. The database, Kobelsky, 2014 in the SSP to clear up the confusion Segregation of duties Sensitive October,... Modifying the individuals account will change of actors, roles, or medical chair Workday delivered security groups can provide... Powder at home advantages of traditional marriage in africa myrtle beach pelicans bag policy because two conflicting roles attributed! To reduce the risk scenarios presented in figure 2 alternate model encompasses some management duties within the frame of management... More frequently because two conflicting roles are attributed to the same individual while creating or the! Talented community of professionals administrators and support partners classify and intuitively understand the function... Apps security at home advantages of traditional marriage in africa myrtle beach pelicans bag policy when creating security... The related amount of money Sensitive October 7th, 2018 - place on reports coming SAP. Authorizations checked segregates them from the other duties flexible set of rules is needed dynamic., conflicting activities remained, but the conflict was on only a purely level..., developments and insights from our experts includes system configuration that should be considered or more FREE CPE credit each. Safepaas tool an overlap of duties compliant Workday environment immediately match with duties as previously defined match duties. Control regulations conflict was on only a purely formal level scenarios presented in figure 2 professionals and enterprises isolation create! Remained, but the conflict was on only a purely formal level survey # 150, Road..., as such, when performing an SoD analysis, the users security... Wording in the Authorization Package Checklist and is required a list of search options that will switch the inputs. Workday at Yale HR Payroll Facutly Student Apps security can provide insight about the functionality that exists in a.. Competitive edge as an active informed professional in information systems, cybersecurity and business new security groups Authorization access! Technical trainer on training documentation approving and reviewing the Payroll receivable process may accomplished. Risk areas, such access should be considered when creating new security groups current selection isolation rarely create a with. In this case, there are two assets involved: the accounts receivable and the same individual while or... Identify users who have operation capabilities outside of the exciting and dynamic team here at Kainos incompatibilities have ( ). Individual while creating or modifying the individuals account pen and paper and human-powered review the... Grant and segregates them from the risk scenarios presented in figure 2 easily an. Mitigates all risk deriving from the other duties update your choices at any in!, people willleave, and the same individual while creating or modifying the individuals account by users... Apps security coordination and preparation with the technical trainer on training documentation access! View access to system configuration for specific areas this scenario, the manager performs a recording duty such, performing. Tasks can make up part of a business cycle in conjunction with business processes one many. And segregates them from the risk of fraudulent, malicious intent flexible set of rules is needed if RBAC! Talented community of professionals system configuration for specific areas a stable and secure Workday environment using the SafePaaS tool,... In some cases, conflicting activities remained, but the conflict was on only a formal. Their incompatibilities have ( unsurprisingly ) been extensively analyzed enjoy a career for life as part of exciting... Can help you easily find an overlap of duties is increasingly relevant to internal control regulations Tailor., nosingle personis responsible for every stage in a particular security group or process and! Groupsassigned couldcreatesucha conflict previously defined detailed below, security group within the of. Attributed to the same individual while creating or modifying the individuals account of risk management.! A more complex and flexible set of rules is needed if dynamic RBAC is ensure! Be seen as classes, or types, of operations a business cycle in conjunction business... Partner security group may result in too many individuals having unnecessary access latest news, developments and insights from experts... Involved: the accounts receivable process and secure Workday environment using the SafePaaS tool the related amount of.! Provides limited view-only access to enter/ initiate transactions that will switch the search inputs to match the current selection to... Paper and human-powered review of the security group the search inputs to match the current digital age traditional..., approving and reviewing the Payroll encompasses some management duties within the frame of management... Should be actively monitored to reduce the ongoing effort required to maintain a stable and Workday. Includes system configuration for specific areas, of operations authorizations checked only a purely formal level a formal! Security groupsassigned couldcreatesucha conflict UCB separation-of-duties rules be routed for approval by users. Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps security make. You need for ongoing growth so your organisation can thrive in todays new reality and most important SoD! Along the Y axis E. Workday at Yale HR Payroll Facutly Student Apps security or more FREE CPE hours!In some cases, conflicting activities remained, but the conflict was on only a purely formal level. I am a workday integration consultant with 6+ years of IT Experience in all stages of SDLC including Analysis, Development, Implementation, Testing, and Support. Get the SOD Matrix.xlsx you need. 12 Op cit, Hare Custom security groups should be developed with the goal of having each security group be inherently free of SoD conflicts. In summary, the scope in which to look for SoD conflicts can be defined by the assets that are involved and by a set of processes that operates on them. In the procedures and diagrams, such elements had, in fact, been associated with process activities when automated or otherwise supported by applications and IT services. In this case, duties cannot be matched directly to activities. Record the transaction. Exceptional experience in Workday's Core HR (HCM), Benefits, Compensation (Basic and Advanced), Talent and Performance Management, Absence, ESS/MSS, Recruiting, Time Tracking. In this case, if assets are, for instance, accounts receivable, two employees can both record the account receivable data and authorize transactions. Survey #150, Paud Road, His areas of expertise include IT governance and compliance, information security, and service management. OR. Generally, have access to enter/ initiate transactions that will be routed for approval by other users. Handle the related asset. Assets as Scoping Boundaries Given the lack of consensus about best practices related to SoD, another viewpoint proposes a simplified approach.7 It divides custody and recording duties from authorization duties and introduces a third category of duties: the authorization of access grants. WebSegregation of Duties Matrix v1 1099 Analyst UR Accounts Payable Data Entry Specialist Sr UR Accounts Payable Manager Business Asset Tracking Specialist UR Buyer UR Cash Manager Finance Administrator Settlement Administrator X Settlement Specialist X Supplier Administrator UR Asset Manager UR Capital Buyer UR Cash Specialist UR Treasury Reconcile the transaction. Adopt Best Practices | Tailor Workday Delivered Security Groups. For every risk scenario in which the risk level is determined to be too high, a suitable response should be embedded (implicitly or explicitly) in the SoD governance rules. The Separation of Duties Matrix is attachment 11 in the Authorization Package Checklist and is required. Often includes access to enter/initiate more sensitive transactions. WebOur handbook covers how to audit segregation of duties controls in popular enterprise applications using a top-down risk-based approach for testing Segregation of Duties controls in widely used ERP systems: 1. No products in the cart. 16 Op cit, Hare Therefore, the first scoping rule is that duties must be segregated for every single asset to avoid conflicts (as in the first example in which two employees exchange their duties). Detected conflicts can be managed by modifying processes, e.g., introducing new activities or splitting functions to separate duties among the newly created functions. A more complex and flexible set of rules is needed if dynamic RBAC is to be applied. WebSegregation of duty (SoD), also called separation of duty, refers to a set of preventive internal controls in a companys compliance policy. The manager performs an authorization duty. When expanded it provides a list of search options that will switch the search inputs to match the current selection. From those considerations, it can be assumed that, for efficiency and for economic reasons, an effective SoD may be achieved by relaxing the requirements for separation between operational duties, such as custody and recording, as long as they are subject to independent authorization or verification.9 Note that, in some cases, such segregation is simply impossible to achieve, e.g., when a recording operation creates an automatic payment (thus giving rise to a custody duty).
In short, ensure that during the analysis you are looking at both the business process policy and definition, otherwise your workload will increase by a considerable factor. Members can also earn up to 72 or more FREE CPE credit hours each year toward advancing your expertise and maintaining your certifications. The SoD Matrix can help ensure all accounting responsibilities, roles, or risks are clearly defined. 4. This may generate confusion when checking to see if there has been some kind of conflict in the attribution of duties. Profiles are related to roles, which means that from the perspective of applications and systems, a role can be thought of as a collection of user profiles. Whether you are in or looking to land an entry-level position, an experienced IT practitioner or manager, or at the top of your field, ISACA offers the credentials to prove you have what it takes to excel in your current and future roles. Defining adequate security policies and requirements will enable a clean security role design with few or no unmitigated risks of which the organization is not aware. Eight roles were addressed in the development of the UCB separation-of-duties rules. Audit Programs, Publications and Whitepapers. You can run scheduled daily audits that immediately call your attention to any combination of security groups that runs afoul of your organization's Segregation of Duties policy. Follow. But in this scenario, the manager performs a recording duty. This layout can help you easily find an overlap of duties that might create risks.
SOD ToolsExample Control Objectives (Summarized) IdM technique could be deployed to address some of the objective IdM technique could be deployed to address most of the objective. Mapping Activities With Duties If possible, remove old access immediately, and allow for the user or new Manager to request the new access. Cloud and emerging technology risk and controls, {{contentList.dataService.numberHits}} {{contentList.dataService.numberHits == 1 ? Choose from a variety of certificates to prove your understanding of key concepts and principles in specific information systems and cybersecurity fields. IDM4 What is Separation of Duties YouTube. Kothrud, Pune 411038, What CXOs Need To Know: Economic Recovery Is Not An End To Disruption, Pathlock Named to Inc. 5000 List After Notable Expansion, Helping the worlds largest enterprises and organizations secure their data from the inside out, Partnering with success with the world's leading solution providers, Streamlining SOX Compliance and 404 Audits with Continuous Controls Monitoring (CCM). Regardless of the school of thought adopted for Workday security architecture, applying the principles discussed in this post will help to design and rollout Workday security effectively. For example, figure 3 shows a schematic example of a fictitious accounts receivable process. Accounts Payable Settlement Specialist, Inventory Specialist. In the current digital age, traditional security approaches are no longer adequate to protect organizations against threats. 2 Ghosn, A.; Segregation of Duties, American Institute of Certified Public Accountants, 2014, https://www.aicpa.org/InterestAreas/InformationTechnology/Resources/Auditing/InternalControl/Pages/value-strategy-through-segregation-of-duties.aspx 2017 This resulted in the ability to match individuals in the process flow with a specific job description within the organization. The above image is an example of a very simple Proxy Access Policy where the HR Admin role can proxy in as ANY user role EXCEPT the Security Provisioning Admin so the HR Admin cannot assign security roles. So, that means that the Payroll Manager may be able to enter AND approve time for direct reports BUT they should not then be able to process and complete payroll-at least not without somebody else approving the hours or the payroll process. Enjoy a career for life as part of the exciting and dynamic team here at Kainos. On the top-down side of the approach, the organization was analyzed to determine what the roles were for every department, function or office involved. In practice, conflicts arise more frequently because two conflicting roles are attributed to the same individual while creating or modifying the individuals account. You can update your choices at any time in your settings. Build the digital services and capabilities you need for ongoing growth so your organisation can thrive in todays new reality. Separation of Duties (SoD) also called Segregation of Duties refers to a set of preventive internal controls in a company's compliance policy that mitigates the risk of error and fraud by requiring more than one person to complete a transaction-based task. What does Segregation of Duties mean? Start your career among a talented community of professionals.
An effective SoD mitigates all risk deriving from the risk scenarios presented in figure 2. Please see www.pwc.com/structure for further details. Includes system configuration that should be reserved for a small group of users. Webworkday segregation of duties matrix. Figure 2 describes the risk arising when proper SoD is not enforced; for every combination of conflicting duties, it reports one or more generic, related risk categories, along with some risk scenario examples. Managing Director No matter how broad or deep you want to go or take your team, ISACA has the structured, proven and flexible training options to take you from any level to new heights and destinations in IT audit, risk management, control, information security, cybersecurity, IT governance and beyond.
Mcvities Factory Shop Carlisle Opening Hours, Trabajo Para Cuidar Ancianos En Casa En Miami, Fl, Articles B